Security solution
10:43 - 27/11/2014
Storage and server technology
Safety system - Lightning protection
ANALOG CAMERA SOLUTIONS
VIDEO CONFERENCE SOLUTION FOR 2 DEMAND POINTS WITH CISCO SX20 DEVICE
Any business operating in any field, when investing in building a complete IT system, is indispensable for security and security solutions for its system. If data center is like the heart of a system, security solutions are a barrier that protects that heart, protecting corporate data, information and systems safe from unauthorized access. from outside and within the business.
Ι. SecurID two-factor authentication solution from RSA
With the traditional, insecure use of authentication, better authentication solutions are needed in today's business environment. An authentication solution is only good when it meets the following key requirements:
- Low cost.
- Easy, convenient for users and can be used in many systems.
- Good scalability and compatibility with other systems.
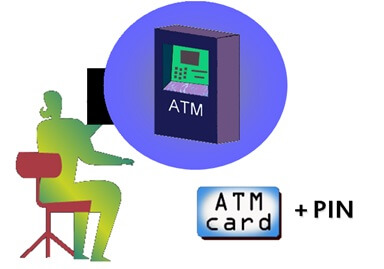
RSA's SecurID two-factor authentication solution works according to the principle: to log into the system, users must have two factors: what they know and what they have. Similar principle when we withdraw money at an ATM, we need an ATM card (what we have) and a PIN (which only we know). Without one of these two factors (ATM or PIN) you cannot withdraw money.
The RSA SecurID® solution consists of three components:
1. RSA SecurID® Authenticators:
Device is attached to the user. They can be either hardware or software and are called tokens. Customers can choose the right equipment for their needs.
If it is a hardware device, RSA's solution allows users to use it anytime, anywhere, on any computer without having to install any additional software (zero footprint solution).
If it is software, they can be installed on a laptop, integrated with a browser or other alternative handheld devices such as PDAs, Wireless Phones, ... These devices generate different numbers. within a certain amount of time.
For service providers to its customers, such as online transactions over the Internet, RSA also provides on-demand authentication codes. This solution allows the authentication code to be sent directly to the user's mobile device or e-mail address during online transactions.
For service providers to its customers, such as online transactions over the Internet, RSA also provides on-demand authentication codes. This solution allows the authentication code to be sent directly to the user's mobile device or e-mail address during online transactions.
2-Factor Authentication
Two-factor authentication model
2. RSA Authentication Agent:
Software that is installed on access points to the network (For example: gateway, VPN, Remote Access Server, ...), servers (servers) and information resources need to be protected by the enterprise. It works like a doorman. When a user's login request arrives, it will receive and pass the login information to the server with RSA Authentication Manager component to perform authentication. Most of the routers, remote access servers, firewall, VPN, wireless access, ... of leading manufacturers in the world have integrated this component in their products. Therefore, implementing the solution of RSA is very simple and easy. This is an extremely important benefit of the RSA SecurID solution.


Software Token
As the administrative component of the RSA SecurID solution, it is used to verify authentication requirements and centrally administer authentication policies across the enterprise network. RSA Authentication Manager can be extended to any need of the enterprise. RSA Authentication Manager is capable of authenticating millions of users, authenticating users on the local network, remote access users, users via VPN, ... RSA Authentication Manager is fully compatible with devices. network, RAS, VPN, Access Point, ... of all major manufacturers in the world. Therefore, with SecurID solution of RSA, users absolutely do not have to worry about compatibility issues.
RSA Authentication Manager also allows tight integration with standard service systems such as RADIUS, LDAP, ... The management of the RSA Authentication Manager component is very easy through a Web interface with decentralized authority for many levels. different administrators.
Another outstanding feature of RSA that no vendor has yet is the ability to create multiple independent workspaces (realm) and the ability to allow up to 15 RSA Authentication Manager servers to operate on one system. Hence, the availability of the system as well as the ability to share the load is greatly enhanced.
RSA Authentication Manager also provides work-flow that allows users to manually register requests or solve problems related to token usage, to misplacement, to forget tokens to get instant access password. . Help greatly reduce the administrator's work.
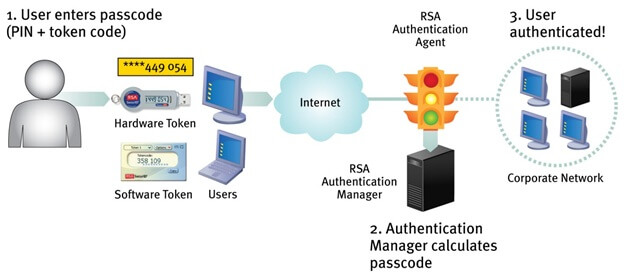
How does RSA SecurID authentication work?
As mentioned above, SecurID consists of three components. Component RSA SecurID Authenticators also known as Token will be given to users. This component comes in different types (be it a hardware token or software token) but each has a function of generating different numbers after a certain amount of time (Usually one minute).
Assuming a user in the system is allocated a token, when logging in to the system, this user will be asked to enter a username (eg JSMITH) and a series of numbers called Passcode. This series of numbers consists of two components, the PIN number and the number appearing on the token (Token code) of that person at the time of login. All of this information (Username and Passcode) is received by the RSA Authentication Agent component and the component will re-send this information to the RSA Authentication Manager. This server will have the user's PIN in its database. In addition, it also has a mechanism that allows it to compute a series of numbers of it. Authentication Manager will pair the PIN number in the database and its serial number and compare it with the passcode provided by the user. If these two numbers are the same, the user is authenticated and allowed to log on to the network. Otherwise, access will be denied. Either access is accepted or not, this information will be sent to the user by the RSA Authentication Manager via the RSA Authentication Agent component.
As described above, user tokens come in many different types. Based on actual needs, an organization when implementing RSA SecurID authentication solution can choose the device that best suits its requirements. The RSA Authentication Agent component can be installed at various points in the system. It can be installed on network access points such as gateways, RAS, VPN, ... as well as installed on Windows, Novell servers, ... and is integrated in all products of manufacturers. major exporters such as Microsoft, Nokia, CheckPoint, Cisco, Nortel ...
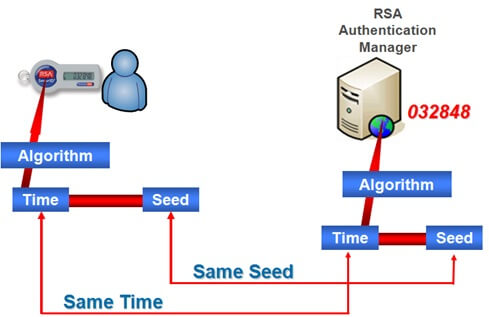
The operating principle of the system
Advantages of RSA SecurID
- High safety: is authenticated based on two factors (PIN + Token code) and always changes, when someone intercepts the user's passcode, it can also be used to log into the system. Therefore, it overcomes a huge disadvantage of password authentication: just blocking the password can be used to login.
- Password management: This is an inherent drawback of passwords. But for SercurID, since centralized authentication on RSA Authentication Manager and Authentication Agent can be installed at many points, even using a token, users can authenticate anywhere in the network, avoid having to use multiple passwords.
- Convenience: With multiple options for RSA SecurID Authenticators, users can choose the most suitable ingredient for themselves.
- Scalability: with RSA Authentication Manager installed on multiple servers, an organization with multiple branches can provide authentication through a replica server located at the branch instead of using using expensive connections to the hub for authentication.
- Active continuity: when a primary server becomes inoperable, a replication server is upgraded to a primary server. This ensures that the system operates continuously and stably.
- Low cost: with no need to use and manage too many passwords, users will not have to ask for support from the technical department, so the costs of technical support decrease and productivity increases up.
IronPort has been a leading provider of anti-spam, anti-virus and anti-spamware devices for organizations ranging from small to Global 2000. IronPort product lines for email security, web security and management uses the SenderBase system (the organization that provides the world's largest threat search data) to analyze the respective web and email behavior of the world, thus making Iron Port devices more resistant to threats. effectively and quickly in the prevention of risks of harmful impacts on the operation of the organizations.
Solution model
Customers can use IronPort as a mail gateway for both inbound and outbound email data.
- For inbound, when email is sent from outside, when it comes to the Router's Public IP, there will be Router NAT to IronPort according to Port 25 so that IronPort will check the Anti Spam or Anti Virus of the email with attachments and then. Go to MailServer.
- In the outbound direction, when the email is sent from the inside out, the email will go to the mail server first, then the mail server will forward the email to Iron Port. Iron Port will scan mail content to check Anti Spam or Anti Virus of emails with attachments before sending them out to the Internet.
In order for Monitor to manage users sending and receiving emails within the same company through the IronPort system, we have the following features that can be applied to users:
- Message Body or Attachments: mail content or attachments
- Message Size: the size of the email
- Attachment Content: Attachment content
- Attachment File Info: Attachment structure information
- Attachment Protected: Attached file is password protected
- Subject Header: the subject of the email
- Envelope Sender: the sender of the email
- Envelope Recipient: email recipient
- Delete mail
- Email quaranties
- Allows sending mail but with warning message.
- Cut attachments from email
- Add header or footer to the email
- Change the recipient's email address
- Automatically send back notifications to email senders when they violate company laws
Ironport can set up detailed rules for each user or a group of users. Suppose we need to track an individual user or a certain department in a company, then IronPort supports LDAP and AD for retrieving information of users or groups. Thus, when a user or a group of users is legally set up on IronPort, every time they send emails outside or receive emails, IronPort "Quaranties" will be "Quaranties" by a backup on IronPort's hard disk. The administrator can accept or reject unnecessary emails when sent to or sent from this user or group.
After having rules and regulations specifically for users, we can monitor statistics status of email sent / received via IronPort device.
Particularly for those who send emails from other systems than from companies such as Gmail, Yahoo, IronPort can only track through the Header of the email including the following information: size and file format attachments, Senderbase score, DNS lookup, header body, sender / recipient email addresses ...
This is a feature of IronPort to help administrators retrieve email header information when sending in or out of IronPort. This feature will help a lot in needing to know why an email cannot be sent out or the user cannot receive email when the email is sent from outside to the system.
Iron Port Senderbase Network
Iron Port's SenderBase is the world's largest email traffic tracking network. With data collection accounting for about 30% of the world's Internet data, IronPort's SenderBase network provides real-time observations of threats from around the world. SenderBase receives contributions from 120,000 global networks to diversify data. This makes Iron Port able to understand and prevent threats that other competitors are not aware of.

Iron Port Anti Spam
To prevent possible spam entering end-user mailboxes, Iron Port implements multi-layered defense that incorporates reputation (weighted) sender filtering in the outer layer combined with analysis. carefully the content of the data packet in the inner layer. This combination helps to fight spam with high accuracy (98% - 99% with error rate less than 1 / 1,000,000) without affecting the performance of the device.
On behalf of the outer layer, Senderbase Reputation's reputation filter will fight Spam based on the sender's information. SenderBase analyzes the sender's address, or IP address and assigns it a score based on an analysis of more than 150 parameters such as the number of emails sent globally (spammers need to send many messages for spam to be effective), Origin of the sender's country, Blacklists IP, where is the domain registered and how long has it been around ...
The score will range from -10 to +10 which is used to control the management of incoming and outgoing emails. If a sender looks like a spammer, the stricter the law applies.
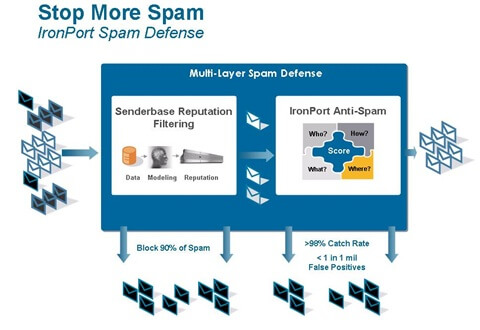
There are two main benefits of SenderBase.
- Iron Port can block 90% of SPAM before it enters the customer's network.
- Mail is blocked by observing the IP address instead of scanning all emails, thereby helping to achieve high performance.
In addition to analyzing the content of the email (what's inside the email), IronPort's technique also analyzes:
- HOW: How emails come about (spammers try to make emails look like they were sent through Outlook, when they may actually have been using some software)
- WHO: Who is sending the email (this is based on reputation scores)
- WHERE: See where the URL is coming from, this is very useful against PHISHING attacks.
Similar to SPAM protection, Iron Port also uses multiple layers of anti-virus.
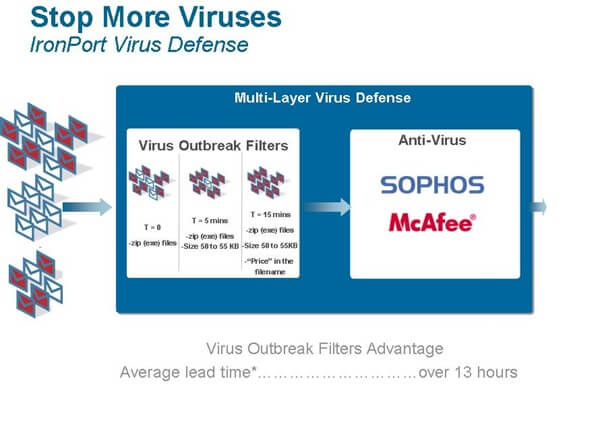
Virus Outbreak Filters utilize Senderbase technology to identify an unusual increase in the number of emails that may contain a virus. Iron Port uses this technique to temporarily hold potentially risky emails until these virus identifiers are released by integrated Anti Virus firms such as McAfee and Sophos. The average time it takes to release a virus signature is about 13 hours. Iron Port therefore provides protection to customers while new viruses develop until an identifier is released.
- Each email sent out will be scanned by IronPort's filter system or filter content. If these emails match the predefined encryption law policy, they will be encrypted - an encrypted email will be sent to the recipient while the decryption key is stored at the Iron key store. Port (Iron Port's Hosted Keys).
- The recipient opens the email using a common email checking software such as MS. Outlook,…, or maybe a web mail.
- The recipient will be asked for a password to open the email. The password is authenticated with the Hosted Keys service. If successful, the decryption key will be sent back to the user and an email will be displayed correctly as to its content.
User management law policy
Customers can create many rules on Iron Port device to manage sending / receiving mail of users.
Async OS - MTA
AsyncOS operating system is an operating system developed by IronPort and has been highly optimized for implementing email protection function right at the gateway. It ensures the availability of external emails, reduces the delay of sending / receiving emails, protects users' email information from being stolen, protects the IP addresses used to send email messages. good price, and provide the ability to clearly monitor the mail system.
Expansion
- We can use multiple IronPort devices and one load balancer to share loads and provide redundancy to handle multiple emails and provide high reliability.
- We can buy more user licenses if there is a need for expansion that the performance of the current IronPort device can still meet.
ΙΙΙ. Solution against data loss - McAfee
End-to-end data loss prevention solutions - McAfee Host Data Loss Prevention
1.1. Overview
Enterprises are facing serious consequences caused by end-user behavior, with the highest risk of sending sensitive data. McAfee Host Data Loss Prevention monitors and prevents user behaviors that can lead to the loss of sensitive data. This protection is done over networks, through applications and mobile storage devices. Administrators have full control over users whether they are at home, at work or on a business trip. Prevent the exposure and theft of sensitive data to employees, as well as hackers to protect business, avoid financial and brand damage.
1.2. Benefits of McAfee Host Data Loss Prevention:
- Limit data transmission via any channel: Monitor and control the copy of sensitive data to removable storage devices, via email as well as messaging programs such as Yahoo Messenger, Hotmail ... as well as through other communication channels
- Comprehensive protection of the organization's infrastructure: securely protect data throughout the organization, at terminals, on servers, at Internet gateways and in the network regardless of operating system or different types of equipment.
- Automated protection: Protects the enterprise's organizational environment against accidental or intentional user data breaches by automatically detecting and enforcing corporate information security policies. Karma
- Centralized Governance with ePolicy Orchestrator (ePO): Arrange risk management of your entire organization's portfolio with McAfee Host Loss Prevention through centralized administrator McAfee ePolicy orchestrator
- Control data transmission: Control employee data transmission over the network, used in applications and copied to removable storage devices; protect data in any format even if it has been edited, copied, pasted, compressed, printed or encrypted.
- Comprehensive device management: With integrated McAfee Device Control provides the ability to restrict data being written to USB drives, iPods and other removable storage devices; Specifies which devices have been approved for or not to be used against any of the Windows standard device specifications.
- Multilayer Protection: Using a DLP Host to prevent data loss from end devices by monitoring and limiting user risky behavior towards sensitive data; When combined with McAfee Endpoint Encryption, data will be encrypted, so businesses will have a perfect layer of protection against data loss.
- Advanced detection and execution mechanisms: Automatically collect sensitive data on hard drives then monitor, store evidence, encrypt, quarantine or delete data such as configurations. On-demand encryption when data is copied to removable storage devices or network drives and blocks file sending via email or uploading to the Web unless encrypted.
- Centralized governance: Define and manage data protection policies, deploy and update McAfee Agent regularly, monitor events in real time, and deliver reports based on organizational requirements. . All of this is managed at the ePolicy Orchestrator centralized administrator. Quickly gather all the information you need to support testing and analysis including sender, receiver, time-of-feature, data evidence, and more.
1.3. Feature:
- Categorize and define sensitive data types: Define sensitive data through the Tagging rule, Classify rule is based on the following elements:
- Application: Based on the application, file type to identify sensitive data
- Location: Projecting resource locations to identify sensitive data. For example: Admin can reorganize the file sharing system so that all important data is marked and monitored for easy and accurate security and data loss prevention policies.
- Content: Based on the content in data files (text pattern, key word, dictionary, ..) to identify sensitive data.
- Typical data loss prevention policies: These policies provide preventive actions, warning (depending on admin settings) when detecting impact, transferring sensitive data that has been typed. sign. Policies will be enforced according to user / group:
- Application File Access Protection rule: keeps track of sensitive marked application file types
- Clipboard Protection rule: policy against copy / past sensitive content
- ScreenCapture Protection rule: Screenprint policy that contains sensitive content
- Printing Protection rule: policy prohibits printing of data (hard copy) containing sensitive content
- PDF / Image Write Protection rule: Policy prohibits printing to pdf / image files of data containing sensitive content
- File System Protection rule: policy to protect and monitor the file system on file server or removable storage device
- Removable Storage Protection rule: Policies that control the transfer of data containing sensitive content to external storage devices
- Network Communication Protection rule: policy against loss of sensitive data over network protocols (protocol / port), IM, upload, etc.
- Email Protection rule: Policy against data loss through outbound channel
- Web Post Protection rule: policy against data loss via web mail: gmail, Microsoft outlook web acess, hotmail, yahoo mail, ...
- Reaction Rule actions for anti-data loss policies: Depending on administrator settings, McAfee Host Data Loss Prevent provides the following typical actions:
- Block: Prevent users' action
- Monitor: logs the user's actions
- Notify user: Displays a message (pop up message) at the users computer
- Encrypt: Encrypt sensitive data
- Store Evidence: Save evidence of user actions in storing sensitive files e.g. saving sensitive file copy sheet, email body, screencapture, etc.
- Monitoring and reporting: McAfee Host Data Loss Prevention provides the ability to track all the sensitive data flow of all users in a detailed, intuitive way, so it is easy to create reports. the type of users' data streams. Reports can be exported as pdf or xls, ..
2. Solution managing device access (McAfee Device Control):
In a survey of companies organized by McAfee, more than 50% of employees admitted using portable storage devices to obtain organizational business information. go out or work from home, in which some data is extremely sensible that bringing out of the corporate organization is a concern of the organization. McAfee Device Control helps businesses monitor and limit copy behaviors on mobile devices for the purpose of preventing loss of organizational sensitive information.
2.1. Benefits of McAfee Device Control:
- Protect the organization from the risk of data loss: Protect the organization's reputation, brand, customer trust, competitive disadvantages, financial losses, and more through star control copy data through external devices
- Enhanced data visibility and control: Monitor and provide policies to regulate how employees use and convert data to external devices such as usb, mp3 player, cd, dvd, blue-tooth wireless device, even behavior control even when employees do not have a network connection to the organization.
- Stay productive: The ability to specify hardware details through filters, monitor and intercept confidential data on any removable storage device, ensuring employees are only allowed to operate safely. all the hardware is designated as part of their daily routine.
- Centralized management: Centralized management with McAfee ePolicy Orchestrator product (ingredient management, centralized integration of McAfee products).
Simple operation compliance control: Admin monitor real-time monitoring, and allows the creation of reports to demonstrate compliance with internal security requirements, employee regulatory audits also like other related departments.
2.2. Feature:
- Comprehensive control over data and peripherals: Control the way users copy data to USB, MP3 players (iPods), CDs, DVDs, blue-tooth devices , infrared, capture device, COM port, LPT, and more, prevent any attempt to copy data that violates organization policy, protects data format even when it is corrected. change. Accurately identify the devices that can and cannot be used by all windows parameters, product ID, vendor, device name, device class, designate devices that can be used, Content can and cannot be copied and used.
- Centralized management: The ability to centrally manage and deploy by organizations, groups, and set policies for each target group, department, as well as each end user.
- Reporting and auditing: The ability to record logs in detail for inspection purposes and as test evidence.
3. Data encryption solution (McAfee Endpoint Encryption):
Along with the increasing data breach, the confidentiality of information and data protection is very important and necessary for businesses and organizations. The McAfee Endpoint Encrytion provides strong encryption and efficient access control features that help prevent unauthorized access to sensitive data areas and information leakage.
3.1. Benefits of McAfee Endpoint Encryption:
- Protect data across all devices: Provides consistent protection of data on desktops, laptops, mobile devices, detachable hardware devices and storage devices mobile storage;
- Information security including data, intellectual property, legal and financial records, confidential records, ..
- Maintain work efficiency: With encryption and decoding virtually not interrupt the work of the user as well as the performance of the system; Allows users to securely access, store, share and transfer data.
- Simplified administration: Easily deploy and enforce security policy, encrypt data, and centralize user authentication - all from the central console; support compliance with internal and external security regulations.
- Reduce costs: integrate end-to-end solutions with service providers; take advantage of existing security products and systems.
- Integration with existing systems: Integrate with McAfee security products and synchronize with Active Directory, LDAP, PKI etc; Supports all Windows operating systems.
3.2. Feature:
- McAfee Endpoint Encryption for PC: Helps prevent the loss of sensitive data on laptops and mobile devices, especially in the event of loss or theft; enforce powerful access control with multiple authentication factors.
- McAfee Endpoint Encryption for File / Folder: Automatically encrypt files and folders when shared or moved in the system; Support unlimited users.
- McAfee Endpoint Encryption for Removable Media (Extension to File / Folder): Protects information stored on mobile devices and media that can connect to enterprise endpoints; Read, edit and save encrypted data without installing any other software.
- McAfee Endcrypted USB: Extends the encryption range for USB devices; easily monitor encryption devices across the enterprise. Protection will be more secure with the McAfee Anti-Virus solution.
4. McAfee Epolicy Orchestrator (ePO) centralized management tool
McAfee Epolicy Orchestrator (ePO) is a centralized management tool for all McAfee solutions, allowing administrators to centralize all McAfee devices and products on a single interface. Administrators can deploy, set up security policies, monitor and report on all McAfee security systems such as Virus, Spyware, Spam, Device control, SiteAdvisor, Endpoint solution, Data, Network, Compliance. ,… If we combine other McAfee solutions, this helps to reduce costs and manpower to operate the system.
EPO Features:
- Integration with Microsoft Active Directory (AD): mapping data from AD to ePO, helping administrators easily and quickly manage and deploy McAfee in the network. The way of organizing and managing users, computers ... in ePO is like Microsoft AD.
- The extended management model can be integrated with other system management solutions such as HP OpenView and BMC Remedy.
- Rogue system dectection: automatically detects and installs virus software on new computers on the network according to the policy set initially.
- Centralized management interface helps administrators quickly identify and understand the relationship between security events in the network.
- Web interface support creates flexibility for administration in a large environment.
- Decentralize monitoring and control for users by product, region, function.
- Automatically generate reports, support customizing the configuration of the administration interface, give a way to quickly display information about network security according to needs.
- Support for multi-level administration model to help reduce network bandwidth during control and update process.


